Where
do Router Interfaces get their names?
Router interfaces get their names when the
router boots. A “device discovery” takes place and the names of the interfaces
are generated based on a predicable method. On fixed interface routers (like the
older 2500 series routers) the interfaces will always be the same. However, on
newer routers like 2600, 3600, 3700, and 2800 series routers, interfaces can be
modular. That means that the interfaces are cards (modules) that can be
“plugged into” the router in different slots. Some of these interfaces are on
WAN interface cards (WIC) and some are on Network Modules (NM). Other router
interfaces will be built right onto the router. The newer model routers have
different names for some of these slots like enhanced network modules (NME) and
high-speed WIC (HWIC). However, for the purposes of naming the interfaces, the
effect is the same.
Interface
Naming Conventions
Cisco router interfaces are named with the
following convention:
Media-type slot#/port#
The media type is Ethernet, Fast Ethernet,
Gigabit Ethernet, Serial, Token-ring, or other media types. You must keep in
mind that a 10Mb Ethernet interface is the only kind of Ethernet interface
called Ethernet. A 100Mb Ethernet interface is called a Fast Ethernet interface
and a 1000Mb Ethernet interface is
called a Gigabit Ethernet interface.
Now let’s talk about the “slot#/port#”
designation. On the old 2500 series routers, they had fixed ports so there was
no slot numbers. Thus, if a 2500 series router had two Ethernet interfaces,
they were called Ethernet0 and Ethernet1.
It is important to point out that Cisco slots and ports always start
with zero first, then one.
On the newer model routers with slots, any
interface built onto the router (a fixed port) is considered to be in slot 0
(zero). This is even true for WAN
interface cards (WIC) slots that are on the router. Any WIC installed in a router is in slot 0. So, the first WIC installed in the router
will always be WIC 0, even if it is in slot 1. This can be confusing
sometimes. So if Slot 0 has a 2 port
serial WIC and Slot 1 had a BRI interface, you have Serial 0/0, Serial 0/1, and
BRI0/0.
Say that you have a Cisco 2610 router. If you put a Serial WIC card in slot zero
(called W0 on the router), that module would be called Serial0/0. If there was
a two port Serial WIC card in the other slot (slot W1), it would be called
Serial0/1 and Serial0/2.
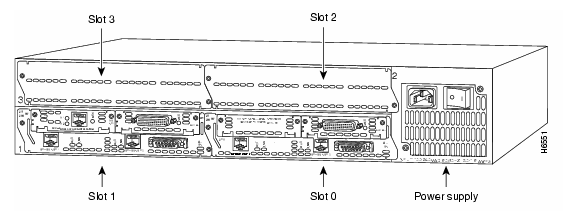
Say that you had a Cisco 3640 router. That
router has 4 NM slots and no built in network interfaces. The network module
numbering on a 3640 starts with zero and goes to three. This number starts on
the bottom right of the router (there are four slots, two and two, each two on
top of the other two) with zero. So, the bottom right slot is slot zero. The
bottom left slot is one, the top right slot is two, and the top left slot is
three. If you put a module with two WIC cards in the top right slot, your WIC
cards would be called Ethernet2/0 and Serial2/0.
Here is a picture showing this layout:
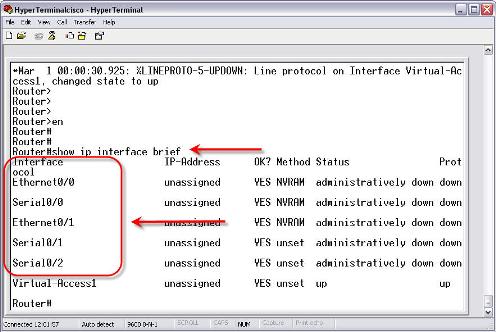
The show ip interface brief command is the most useful command to see what interfaces are on the router and what their names are. Here is an example:
This command output is from a Cisco 2611
router. It has two built in Ethernet interfaces and two WIC slots. In the first
WIC slot is a single port Serial module. In the second WIC slot is a two port
serial module. You can see how the naming we have been talking about applies to
these modules.
If I were to turn off the router, remove the two port serial interface, and reboot the router, you would see that the configuration for those modules has disappeared. Thus, if I were to save that configuration, turn off the router, replace the two port serial module with a good module, and reload the router. The configuration for those two serial modules would be lost. This is another important reason to always have a good backup copy of your Cisco IOS configuration.
Quick
overview what you got from the article above:
- The network interface naming depends on the type of router you have and what slots are on that router.
- Interface numbering starts at zero and goes up.
- Router network modules are named zero and go up, starting with the bottom right slot.
- Be familiar with the models of routers you use and how their slots are laid out.
- All built in interfaces on a modular router and all WIC cards are considered to be in slot 0.
- When in doubt, look at the router and how its slots are labeled and do a show ip interface brief to see what slots were found. Preferably, you should match up the physical slots and interfaces with the named interfaces before making any changes on that router.